-
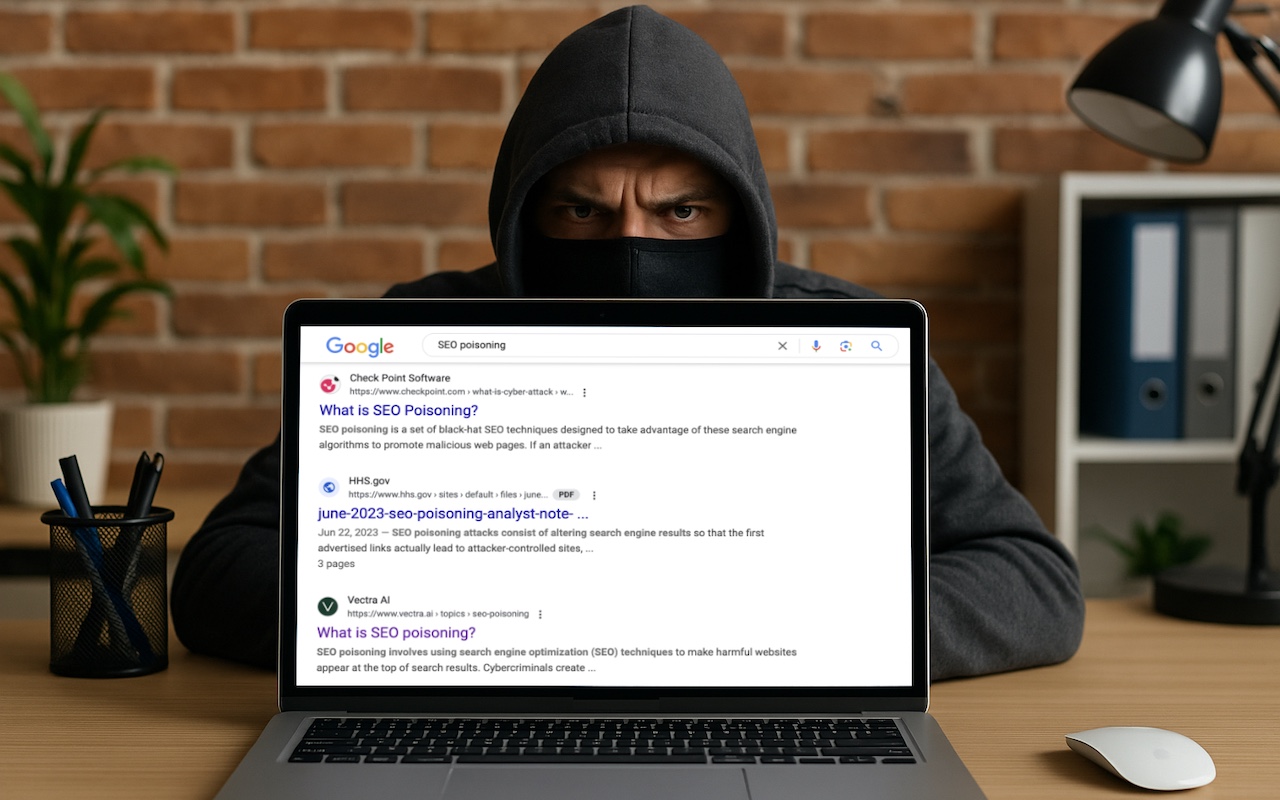
Don’t Assume That Top Google Search Results Are Guaranteed Safe
We hate to encourage paranoia, but all is not well with Google Search. Recently, we’ve heard of multiple instances where people were nearly taken advantage of due to relying on the top result in a Google search. In one case, a user called a purported HP support phone number directly from the search results but ended up speaking with a scammer. In another, a user thought they were downloading th... Read more -
Never Save Your Work in These Locations
In every job that involves interaction with the public, amusing “Can you believe…” stories about customers abound. They’re often triggered by seemingly reasonable behaviors that experts recognize as problematic. A well-known example from the early days of personal computing is a college student who kept track of his floppy disk by attaching it to his fridge with a magnet, not realizing that mag... Read more -
In Times of Uncertainty, Increase Your Digital Privacy and Security
With so many troubling things happening in the world, some clients have inquired about ways to enhance their security. While we don’t want to encourage paranoia, there are many legitimate threats, and everyone will have their own levels of worry about each one. The effort and inconvenience that different people are willing to endure also vary. Higher levels of security often necessitate sign... Read more -
Businesses, Don’t Overlook Email Backup
Cloud-based email services such as Google Workspace and Microsoft 365 dominate the market for organizational email for good reason. Dealing with the constant onslaught of spam and online attacks is hard, as those traumatized by running mail servers in the “good old days” can attest. While email service providers excel at ... Read more -
When Purchasing a Fireproof Safe, Pay Attention to the Details
The devastating losses caused by the Los Angeles wildfires have underscored the need to protect data from catastrophic events. A traditional offsite backup—periodically moving a hard drive to another location—might not have sufficed in areas affected by wildfires, where many structures were destroyed. An online backup using a service like Read more -
The Importance of Properly Offboarding Employees
Employers and their employees part ways for all sorts of reasons. People may move on because of a contract’s completion, to take a new job, or because they’re retiring. Employees may also leave due to being laid off or fired. Whatever the reason, offboarding—the process of managing an employee’s departure from an organization—is essential. Without a systematic offboarding protocol, or... Read more -
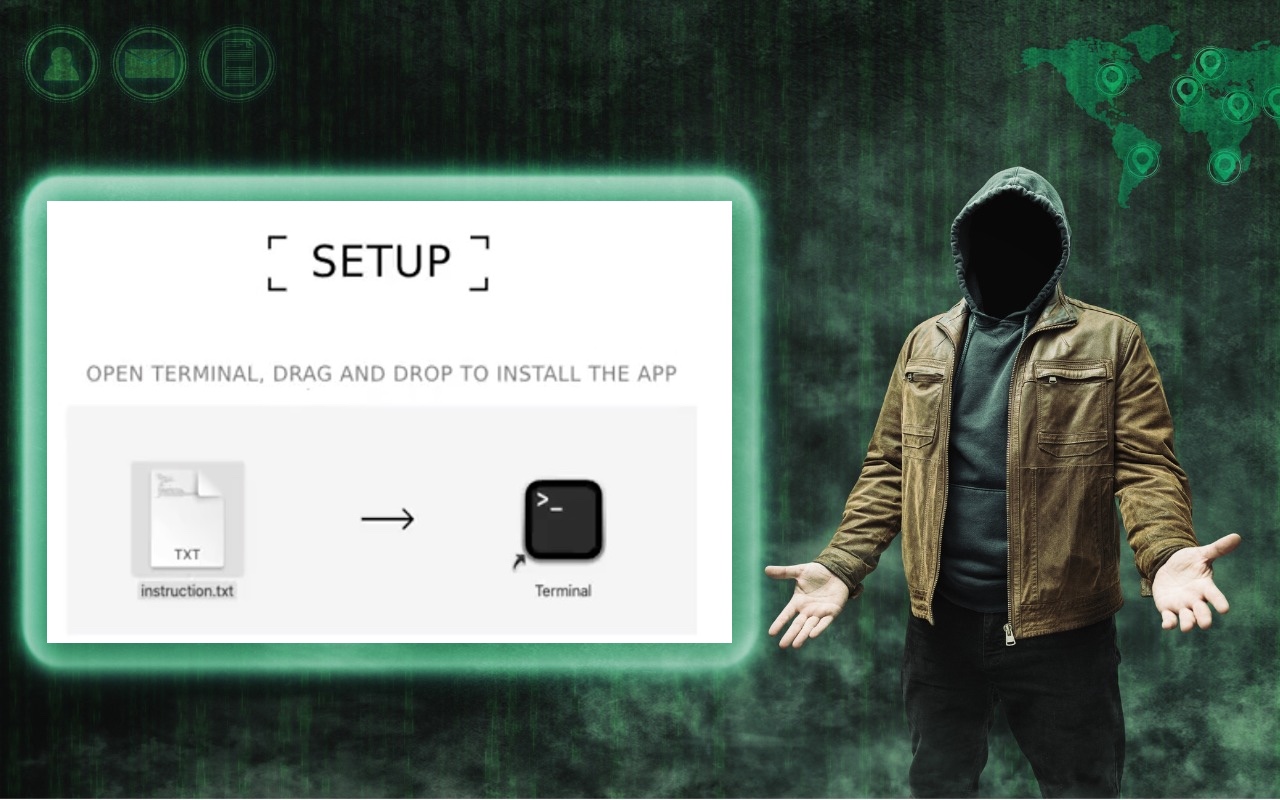
Don’t Listen to Anyone Who Tells You to Drag a Text File into Terminal
In macOS 15 Sequoia, Apple made it more difficult to bypass Gatekeeper to run apps that aren’t notarized. (Notarization is one of the ways Apple ensures that apps distributed outside the Mac App Store are unmodified and free from malware.) Cybercriminals have responded to this increase in security with a new social engineering attack. They provide the victim with a disk image, ostensibly to ins... Read more